The Hidden Threat Lurking in Your Living Room
Security researchers have issued a critical warning regarding certain unverified Android TV streaming boxes sold through major retail channels, including prominent U.S. stores. These devices, often marketed with the lure of providing unauthorized, free access to thousands of premium streaming channels and pay-per-view events, harbor a sinister secondary function: they are secretly being enrolled into large-scale botnets used to launch malicious cyberattacks.
The investigation, initially highlighted by security journalist Brian Krebs, focuses on devices like the Superbox and similar gray-market streaming hardware. While consumers believe they are purchasing a simple media player, they are unknowingly introducing a compromised device into their home network, posing significant risks to personal security and global internet stability.

The Dual Deception: Illegal Streams and Botnet Operations
The appeal of these compromised streaming boxes is their promise of illicit content. Devices like the Superbox advertise access to over 2,200 pay-per-view and streaming services for a one-time fee, bypassing legitimate subscription costs. This illegal functionality serves as the perfect camouflage for the device’s true malicious purpose.
Experts explain that the core issue lies in the pre-loaded, modified firmware these boxes run. Unlike certified Android TV devices from established manufacturers, these gray-market boxes utilize deeply customized operating systems that contain backdoors and hidden code. This code allows remote attackers to seize control of the device without the user’s knowledge.
How Streaming Boxes Become Botnet Nodes
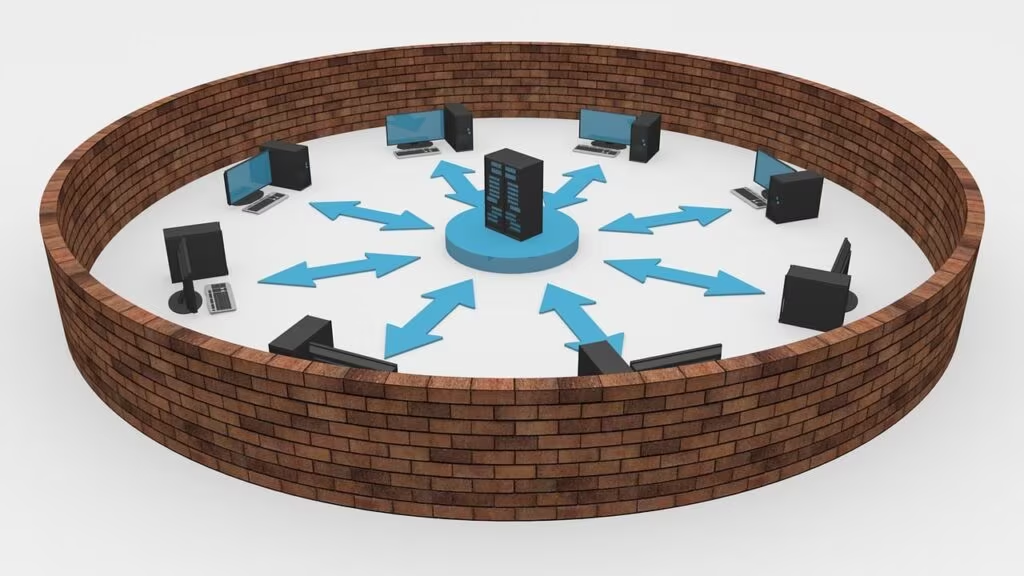
A botnet is a network of private computers infected with malicious software and controlled as a group without the owners’ knowledge. These compromised streaming boxes are ideal targets because they are:
- Always Connected: They remain powered on and connected to the internet, often 24/7.
- High-Bandwidth Users: Their primary function (streaming) requires robust internet connections, making them powerful nodes for attacks.
- Unmonitored: Most users never check the background processes or network activity of their streaming device.
Once compromised, the boxes are typically used to participate in Distributed Denial of Service (DDoS) attacks. In a DDoS attack, thousands of devices simultaneously flood a target server (like a bank, government website, or major corporation) with traffic, overwhelming it and forcing it offline. The owners of the streaming boxes are unwitting participants in these major cybercrimes.
“The irony is that consumers buying these boxes to save a few dollars on streaming subscriptions are effectively paying to become foot soldiers in global cybercrime operations,” noted a security analyst familiar with the investigation.
Risks to Consumers: Why You Should Care
The presence of a botnet node on a home network carries several immediate and long-term risks that extend far beyond just consuming bandwidth.
1. Network Vulnerability
The malicious firmware on the streaming box often grants attackers deep access to the device’s operating system. This level of compromise can potentially allow the attacker to pivot from the streaming box to other devices on the same local network, such as computers, smartphones, or network-attached storage (NAS) drives, leading to data theft or further infection.
2. Bandwidth and Performance Degradation
When the device is actively participating in a DDoS attack, it consumes massive amounts of upload bandwidth. This can severely slow down internet service for the entire household, impacting work-from-home activities, online gaming, and legitimate streaming services.
3. Legal and Reputational Risk
While the user is unaware of the malicious activity, the IP address associated with the DDoS attacks traces back to the consumer’s home. In severe cases, this could lead to law enforcement investigation or, at the very least, having the user’s Internet Service Provider (ISP) flag the account for suspicious activity and potentially throttle or suspend service.
Protecting Your Home Network from Compromised Devices
For consumers who may have purchased unverified or gray-market streaming boxes, immediate action is necessary. The primary defense is isolation and removal.
Actionable Steps for Device Owners
- Disconnect Immediately: If you own a device like the Superbox or any unbranded streaming device purchased primarily for accessing illegal content, disconnect it from your network and power source immediately.
- Network Monitoring: Check your router logs or use network monitoring tools to look for unusually high upload traffic, especially when the device is supposedly idle.
- Network Segmentation (Advanced Users): If you must use unverified smart devices, place them on a separate, isolated Guest Network or a dedicated VLAN (Virtual Local Area Network). This prevents the compromised device from communicating with your primary computers, storage, and financial data.
- Factory Reset is Insufficient: Be aware that a simple factory reset may not remove the malicious firmware, as the compromise is often embedded at a deeper hardware or bootloader level.
- Choose Verified Hardware: Stick to streaming devices from reputable manufacturers (e.g., Google, Amazon, Roku, Apple, Nvidia) that receive regular security updates and adhere to strict hardware certification standards.
| Device Type | Risk Profile | Mitigation Strategy |
|---|---|---|
| Unverified/Gray Market Boxes (e.g., Superbox) | High (Pre-loaded malware, no updates) | Disconnect immediately; do not use |
| Certified Android TV (e.g., Shield, Chromecast) | Low (Regular security patches) | Ensure automatic updates are enabled |
| Other Smart Devices (IoT) | Moderate (Varies by manufacturer) | Isolate on a guest network; change default passwords |
Key Takeaways
The discovery that widely available streaming boxes are being weaponized underscores the critical importance of supply chain security in consumer electronics. For the average user, the lesson is clear: the promise of “free” premium content often comes with a hidden, high cost—the compromise of your home network and participation in cybercrime.
- The Threat is Real: Specific unverified Android streaming boxes are being used as nodes in massive DDoS botnets.
- Retail Presence is Misleading: The fact that these devices were sold at major retailers does not guarantee their security or legitimacy.
- Risk Extends Beyond Bandwidth: Compromised devices threaten the security of all other computers and data on the local network.
- Immediate Action Required: Owners of suspicious, gray-market streaming boxes should disconnect them and consider replacement with certified hardware.
Conclusion
As the Internet of Things (IoT) continues to expand, every connected device—from smart refrigerators to streaming boxes—represents a potential entry point for attackers. This incident serves as a crucial reminder that consumers must prioritize security over convenience or cost savings, particularly when dealing with hardware that promises unauthorized access to copyrighted content. Choosing certified, regularly updated hardware remains the most effective defense against becoming an unwitting participant in the next major cyberattack.
Originally published: November 24, 2025
Editorial note: Our team reviewed and enhanced this coverage with AI-assisted tools and human editing to add helpful context while preserving verified facts and quotations from the original source.
We encourage you to consult the publisher above for the complete report and to reach out if you spot inaccuracies or compliance concerns.